Protect your Linux OS with the best malware scanners: top picks for 2025
A Linux malware scanner is an additional security layer designed to detect and neutralize threats that could compromise your system. Finding a suitable malware scanner for your Linux servers isn’t always easy with how many options there are in the market.
No worries, though – this article will help you out by highlighting the top malware scanners for Linux in 2025, ensuring you choose a tool that is robust, reliable, and suited to your specific needs.
Why Linux systems need malware scanners
Despite Linux’s reputation for security, no operating system (OS) is immune to the risks posed by malware. Malware scanners are essential for identifying hidden threats, preventing data breaches, and maintaining system integrity.
Many Linux malware scanners are designed to detect and neutralize a wide range of threats, including viruses, trojans, worms, rootkits, and spyware. They also offer real-time protection against new and emerging threats, ensuring that your system is always defended.
With Linux’s increasing popularity, it’s more important than ever to have a reliable and effective malware scanner. This is especially true for environments using Virtual Private Servers (VPS), where installing a malware scanner is considered one of the best security practices.
Top 4 malware scanners
Now, let’s dive into the top four malware scanners for Linux. We’ll explore the unique benefits of each tool to ensure you have the information needed to choose the right scanner for your security needs.
1. Monarx
- Rating: 4.7/5
- Notable features: Real-time threat detection, automated malware removal, and web application protection.
- Best suited for: Businesses or individuals with high-traffic websites and eCommerce platforms.
Monarx is a proactive malware protection tool specifically designed for PHP-based applications. It operates directly on the server, providing real-time detection and automatic elimination of threats without requiring manual intervention.
Security solutions can strain server resources, but Monarx’s cloud-based approach tackles this. By shifting malware analysis to Monarx’s servers, your VPS can focus on hosting for peak performance.
Since Monarx’s malware detection and removal works automatically, it doesn’t have a command line interface (CLI). This makes it ideal for businesses that don’t have dedicated IT teams or technical staff to manage security.
Aside from malware scanning, Monarx also offers:
- A firewall feature that monitors incoming and outgoing traffic.
- Email alerts for malware scanning results.
- Behavior-based AI Detection that blocks 40% more malware.
- Customizable Linux systems scanning schedule.
These extra features allow you to stay aware of potential threats and take proactive measures to protect your website.
Monarx comes pre-installed on Hostinger’s VPS plans, providing an additional layer of protection for your website.

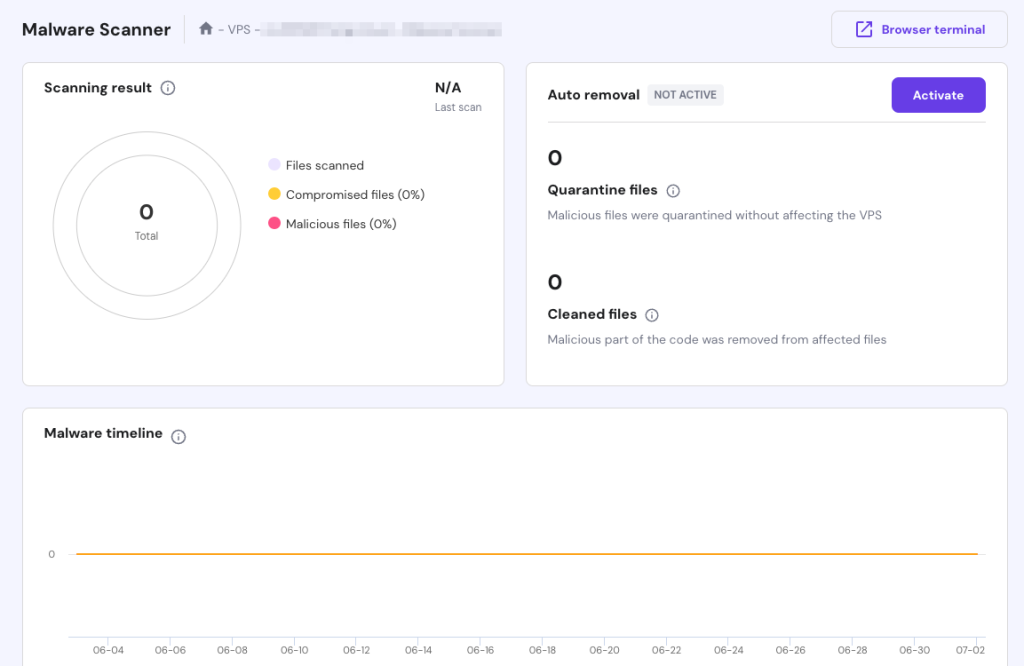
You can also find Monarx on Hostinger’s custom control panel, hPanel. This integration allows you to access and manage your malware-scanning activities directly from the dashboard. On your website’s hPanel dashboard, go to Security → Malware Scanner.
There, you can view the scan results and malware timeline and activate the auto-removal feature.
Monarx’s versatility extends beyond specific platforms or applications. Apart from safeguarding the Linux OS, it also secures open-source applications or codebases running on your Hostinger VPS.
If you’re not using Hostinger, the regular price applies. Monarx offers three pricing plans based on the number of users per server. For servers with up to 20 users, it costs $15/month. For 20 to 199 users, the price is $35/month, and for 200 or more users, it’s $50/month.
2. ClamAV
- Rating: 4.6/5
- Notable features: Open-source, multi-threaded scanning, automatic virus database updates.
- Best suited for: Home users, businesses, and educational institutions looking for a flexible and reliable malware protection tool.
ClamAV is an open-source antivirus engine renowned for its ability to detect a wide array of malware, including viruses, trojans, and worms.
What sets ClamAV apart is its versatility as both a standalone scanner and a server-side email scanner. As a standalone scanner, ClamAV can scan individual files or entire directories on your computer.
As a server-side email scanner, ClamAV can be integrated with popular mail transfer agents like Postfix and Sendmail to scan incoming and outgoing emails for malware automatically.
Combined with its robust community-driven updates, ClamAV ensures timely defenses against new threats. Additionally, you can export other Linux security tools to ClamAV, such as Linux Malware Detect.
Its CLI allows for integration into automated scripts, making it a favorite among system administrators. ClamAV also offers automatic virus database updates, ensuring that the latest malware definitions are always in place.
For home users, ClamAV offers a lightweight and graphic user interface (GUI) alternative called ClamWin. It provides real-time scanning, scheduled scans, and quarantine options for infected files.
3. Chkrootkit
- Rating: 4.5/5
- Notable features: Detects over 70 known rootkits, simple user interface, lightweight, quick scanning process, and can be run from live environments.
- Best suited for: System administrators and security professionals who require a reliable tool to assess system integrity quickly.
Chkrootkit specializes in the detection of rootkits, which are tools used by hackers to disguise their presence on an infected system. Its streamlined functionality makes it a favorite for rapid diagnostics and emergency security assessments.
One of Chkrootkit’s greatest benefits is its lightweight nature. It can quickly scan Linux servers without slowing them down or disrupting regular operations.
Chkrootkit identifies over 70 known rootkits by using various detection methods, including searching for suspicious strings in the kernel modules, checking file permissions, comparing checksums against known good values, and looking for hidden processes.
In addition to Linux systems, Chkrootkit has been tested on FreeBSD, OpenBSD, NetBSD, Solaris, HP-UX, Tru64, BSDI, and Mac OS X. This wide range of compatibility makes it a versatile and reliable tool for system administrators and security professionals alike.
Additionally, you can run Chrootkit from live environments such as USB drives or CD-ROMs, which makes it an ideal tool for emergencies or when dealing with systems that cannot be booted.
4. Lynis
- Rating: 4.4/5
- Notable features: Open-source, extensive security auditing, compliance testing.
- Best suited for: System administrators and security professionals who require detailed audits and reports.
Lynis is an open-source, command-line tool. It detects malware and other potential security vulnerabilities and recommends actions to improve Linux system security. It’s ideal for security professionals who need a comprehensive security audit tool.
One of Lynis’ main advantages is that it’s suitable for penetration testing, security auditing, system hardening, and vulnerability scanning. It can also check for common security issues, such as incorrect file permissions, outdated software versions, and open network ports.
Due to its command-line interface, Lynis may not be suitable for beginners or those who prefer a GUI. It also requires some basic knowledge of Linux security to use effectively. Lynis’ documentation provides basic commands, suggestions, and more details to help you get started.
Overall, Lynis is a powerful tool for experienced Linux users who want to proactively secure their systems and ensure they are in compliance with industry standards.
Lynis is a free tool with the option to upgrade to Lynis Enterprise for enhanced features. This upgrade provides additional security tests, plugins, and overall benefits. Two pricing plans are offered for SaaS or self-hosted platforms.
The SaaS Premium plan costs $3/month per system, whereas custom quotes are available for self-hosted options. There’s a demo available to learn more about Lynis Enterprise.
Conclusion
Malware scanners for Linux systems are essential for maintaining the security and integrity of your systems. Each of the top four vulnerability scanners we’ve discussed has its strengths, tailored to different needs and user levels:
- Monarx – best for automatic security updates, integrated with Hostinger’s VPS plans, ideal for hands-off, continuous protection.
- ClamAV – best for email servers and network file scanning, offering robust, multi-purpose malware detection.
- Chkrootkit – best for scanning rootkits and backdoors, perfect for targeted deep scans of Linux systems.
- Lynis – best for experienced Linux users who require comprehensive security auditing and compliance checking.
Choosing the right malware scanner depends on your specific requirements, expertise level, and the nature of your environment. Remember, proactive security measures not only protect your systems but also preserve the trust of those who rely on your services.
Best Linux malware scanners FAQ
Discover answers to the most common questions about Linux malware scanners.
How to remove malware detected by a Linux scanner?
After detecting malware, Linux scanners usually offer options to delete or quarantine the infected files. Follow the scanner’s prompts or consult the documentation for specific removal instructions. For stubborn malware, additional tools or manual removal might be necessary.
What is the best Linux malware scanner for beginners?
Monarx is recommended for beginners, particularly those managing PHP-based websites or applications. It stands out for its user-friendly approach, offering automatic malware detection and removal, which minimizes the need for manual oversight.
Who offers support and assistance for Linux users regarding malware scanning?
Software developers often provide support for Linux malware scanning directly through their official websites. Additionally, many Linux communities and forums offer user-driven support and troubleshooting advice, which helps resolve issues and gain tips on effective malware management.